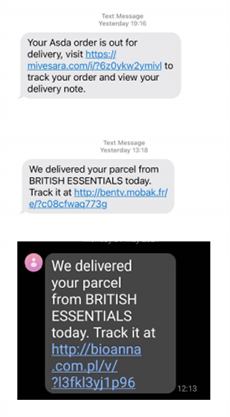
Virgin Media Security Alerts

FluBot Android Malware
What is FluBot Malware?
|
What is a Chargen Vulnerability alert?
You may have recently received a letter or an email from Virgin Media explaining that we have been notified that a device on your network has a Chargen vulnerability. If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
Chargen (Character Generator Protocol) is intended for testing purposes. A system set up to act as a Chargen server responds to queries over port 19 by sending arbitrary characters to the connecting host and continues until the host closes the connection.
If the Chargen service is left enabled it can be abused to participate in online abuse.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have a Chargen vulnerability.
For more information on these reports please visit chargenscan.shadowserver.org*
This could be your Virgin Media Hub 3 or Super Hub, third party home router or any device connected to your home network which allows open communication on TCP/UDP port 19 (Chargen).
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article.
What can I do about it?
We're here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure home network.
*These links to external sites are provided as a courtesy. We are not responsible for the content of these sites or any problems encountered while applying their advice. Unfortunately we are not able to provide any technical support for these issues.
Receiving a Ghost Push Malware alert
You may have recently received a letter and/or email from Virgin Media explaining we've been notified that an Android device on your network contains malware named Ghost Push. If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
Ghost Push is a form of Trojan that specifically targets the Android operating system. The malware is mainly distributed through applications downloaded from untrusted third parties, but can also be hidden in applications downloaded from official markets such as Google Play.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that are infected with malware. They have notified us that an Android device on your home Internet connection (or one connected to your home network) is infected with malware.
Your financial transactions and personal data could be at risk. It is therefore important that you follow the advice in this article.*
Want to fix the issue yourself?
We’re here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure your home network.
Please apply these steps in order:
The easiest way to do this is by using an anti-virus scanner; some suggested are;
You can find these and other virus scanners on the Google Play Store.
Check Point, a threat research and security insights blog, provides a website where it’s possible to check if your Google account has been affected by Gooligan:
2 - Restore to Factory settings
If it is found that your device has the Ghost Push malware, the only method to completely clear your device of the infection is to restore to factory settings. However, it is very important to note that restoring your device to factory settings will delete all of your personal data.
For information on how to perform a factory reset, please refer to the user manual for your device or consult the manufacturer’s website.
3 - Flash the firmware
If a complete factory reset does not completely removed the infection, it may be necessary to re-flash the firmware on your device, this will essentially reinstall a clean version of the operating system. This is a complex process and we recommend taking your device to a certified engineer.
4 - Change your Google account passwords
Changing the passwords for your Google accounts will reset the authorisation tokens for your device. This will ensure that any tokens obtained by the malware will no longer be valid and will prevent malicious third parties from continuing to access your accounts.
How can I protect myself in future?
- 1. Ensure your operating system (OS) is up-to-date
- 2. Install an anti-virus and have it automatically scan your device on a regular basis
- 3. Only download applications from Google Play or trusted third parties
- 4. Read reviews of the applications you want to download. If the application asks for too much personal data or for permissions that it doesn’t need, avoid it.
Receiving a Wannacry Ransomware alert
We have been alerted that one or more of your devices has become infected with WannaCry ransomware, a type of malicious software that encrypts all the information held on your device and demands a ransom payment in order for the files to be unencrypted.
Overview
A device running on your home network has been identified as communicating with criminal infrastructure associated with the WannaCry malware. This means a device on your network is very likely to be infected.
When we suspect that a customer of ours has become infected with ransomware we will send them an alert giving an overview of the ransomware and advice on what to do next.
What has happened?
Virgin Media and its network are not impacted by the ransomware attack.
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be infected by malware. They have notified us that a device on your home Internet connection (or one connected to your home network) is infected with malware.
It is therefore important that you follow the advice in this article.
What can I do about it?
We're here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to deal with this problem.
If a device on your network has already been encrypted by the ransomware, please follow the advice in Scenario 1. An encrypted device will display an on-screen prompt advising your files have been encrypted and can no longer be accessed.
Should none of your devices be showing signs of already being encrypted, it is crucial that you follow the advice in Scenario 2 immediately.
Scenario 1 – A device on my network has been encrypted
If a device on your network is showing a display stating its files have been encrypted there is unfortunately a limited number of options available to you. We recommend you follow the advice in the article below, however please note this is generic advice and may not be specific to your infrastructure or setup. Please proceed with caution.****
- We don’t recommend you pay the ransom because not only will you will help the criminals get what they want but there is no guarantee that your files will be made accessible again. There is nothing stopping the criminals from taking your money and leaving your files in an inaccessible state
- Keep your important files in case a decrypting tool becomes available. Check nomoreransom.org* regularly to see if they have released
- If you have a backup of your system then restoring your system from backup should get things back to normal
For more information on ransomware and how you can protect yourself in future please visit nomoreransom.org*
Scenario 2 – None of my devices are displaying a WannaCry encryption screen
If none of your devices are displaying a WannaCry encryption screen we recommend you follow the advice below. Please note this is generic advice and may not be specific to your infrastructure or setup. Please proceed with caution.**
Perform a Windows Update
Keep your operating system and application software up-to-date. The WannaCry ransomware spreads using a vulnerability in outdated versions of the Windows operating system.
Install software patches so that attackers can't take advantage of known problems or vulnerabilities. Many operating systems offer automatic updates. If this option is available, you should enable it.
Check to see if your device has a virus
The best way to do this is by using an online virus scanner, some good free ones are:
- microsoft.com/security/scanner*
- Virgin Media Internet Security
- eset.com/onlinescan*
- bitdefender.co.uk/scanner/online/free.html*
Use your Internet Security package to remove the virus
If you have an existing security package installed, please consult the instructions on how to remove infections from your device.
If you don't have an existing security package, Sign into your My Virgin Media account and register for Virgin Media Internet Security to start your 3-month trial today.
No bank or credit card details are needed upfront for the trial.**
Once downloaded and installed it will immediately run a scan of your device.
If you already use Virgin Media Internet Security, make sure "Viruses and spyware scanning" is turned on.
Back up your important data
If you haven’t done so already, regularly backup all your information. If the data is stored elsewhere, it will be easier to restore in the case of a future ransomware attack.
Scenario 3 – I administer a network of Windows systems (Advanced)
If you are a Windows system administrator with a number of systems vulnerable to this attack on your network, we recommend you read the advice below. Please note this is generic advice and may not be specific to your infrastructure or setup. Please proceed with caution.****
Deploy the relevant security patches on your Windows systems
The NCSC advise the following steps be performed in order to contain the propagation of this malware:
- Deploy patch MS17-010 here: technet.microsoft.com/en-us/library/security/ms17-010.aspx*
- A new patch has been made available for legacy platforms, and is available here: blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks*
- If it is not possible to apply this patch, disable SMBv1. There is guidance here: support.microsoft.com/en-us/help/2696547*
- and/or block SMBv1 ports on network devices [UDP 137, 138 and TCP 139, 445]
If these steps are not possible, propagation can be prevented by shutting down vulnerable systems.
For more information see: ncsc.gov.uk/guidance/ransomware-latest-ncsc-guidance*
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
VPN Filter Malware alert
Recently, you may have received a letter and/or email from Virgin Media explaining we’ve been told that an online device on your network contains the malware VPNFilter. If you’ve received this from us, please follow the advice on this page to help fix the problem.
Overview
VPNFilter is a form of malware that specifically targets networking equipment running on a home network – specifically internet routers and Network Attached Storage (NAS) devices.
If we think that a customer has become infected with malware, we’ll send them an alert giving an overview of the malware infection and advice on what to do next.
What’s happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the internet that are infected with malware. They’ve let us know that a device connected to your Virgin Media broadband is infected with malware.
We’re unable to specify exactly which device in your home is infected, but it’s likely to be either a Network Attached Storage (NAS) device or an internet router that’s not been provided by us.
To ensure your personal and financial data isn’t compromised, you’ll need to follow the steps below to remove the malware as soon as possible.
What can I do about it?
If you know a few of the basics when it comes to computers and connected devices, there are a number of steps you can take to secure your home network. *
Please select a scenario that fits your situation:
1. I use a router not supplied by Virgin Media
If you’re using a 3rd party router in conjunction with your Virgin Media Hub, it may be infected with the VPNFilter Malware. To remove the infection, please follow the below steps in order:
Remove the router from your Virgin Media Hub
Disconnect the 3rd party router from your Virgin Media Hub so that it disconnects the affected router from the internet.
Factory reset the router
In order to successfully remove the malware from the router, a full factory reset is required to bring it back to its default settings. Most routers will allow you to do this through the same configuration page that you may use to change your wireless password and network name.
For specific instructions on how to do this, please refer to the manual that came with your router or contact the manufacturer. Please note that this action will remove any custom data or settings from the device.
Change the admin password for your router
It’s likely that the default admin password was used by a 3rd party to log in to your router to install the VPNFilter malware. These default passwords are often used for many systems provided by the same manufacturer, so they’re not unique.
To avoid being infected again, we recommend changing the admin password used to access your router’s admin pages to something that’s unique to you.
Update the software on your router
It’s also possible that a malicious 3rd party exploited a known security flaw present in an older version of the software running on your router in order to gain access and install the malware.
Updating the software/firmware on your router to the latest version is the best way of protecting your device from being infected again in this manner. We also recommend enabling automatic updates if this option is available in order to help keep your router up to date.
For specific instructions on how to do this on your router, please refer to the manual that came with your router or contact the manufacturer.
Change any ‘default’ passwords used by other devices
To best protect all the devices in your home from future security issues, we strongly recommend that you change the default passwords of any devices connected to your home network.
Devices that are commonly sent with default passwords are internet connected appliances such as routers, Network Attached Storage (NAS) devices and CCTV systems.
For specific instructions on how to do this for these devices, please refer to the manual that came with the device or contact the manufacturer.
Disable remote access
It’s also recommended to turn off remote access/remote management if you don’t have reason to access your router outside of your home.
Remote access is generally disabled by default, but if you’re unsure how to check this on your router or for specific instructions on how to disable it, please refer to the manual that came with your router or contact the manufacturer.
2. I’m using a Virgin Media provided router only
If you’re using a Virgin Media Hub, you can rest assured that we have no evidence to suggest your router is vulnerable to being infected with VPNFilter.
If the malware has been detected on your home network, it may be present on a Network Attached Storage (NAS) device running in your home. There’s no evidence to suggest other types of internet connected devices are being targeted by this malware.
To remove the infection, please follow the below steps in order:
Backup any data you want to keep
Before taking steps to remove the Malware from a Network Attached Storage (NAS) device in your home, we strongly recommend you backup any data you want to keep from the device as removing the VPNFilter malware infection will involve restoring your NAS device back to factory settings.
The method for backing up data from your NAS device to a computer varies between different makes and models of NAS devices, for specific instructions on how to do this for your device please refer to its manual or contact the manufacturer.
Factory reset your NAS device
Please note this step will remove ALL the data stored on your NAS device, this may include any photos, videos or other files that you may have uploaded to it. Please backup your data.
In order to remove the VPNFilter infection from your NAS device, it will need to be restored to factory settings. Most systems will allow you to do this through the same configuration page that you may use to configure other parts of your NAS device.
For specific instructions on how to do this, please refer to the manual that came with your system or contact the manufacturer.
Please note that simply rebooting the device will be insufficient, a full factory reset is required to completely remove the infection.
Change the admin password for your device
It’s likely that the default admin password was used by a 3rd party to login to your system to install the VPNFilter malware. These default passwords are often used for many systems provided by the same manufacturer, so they are not unique.
To avoid being infected again, we recommend changing the admin password used to access your system’s configuration page to something that’s unique to you.
Update the software/firmware
It’s also possible that a malicious 3rd party exploited a known security flaw present in an older version of the software running on your system in order to gain access and install the malware on your NAS device.
Updating the software/firmware on your NAS device to the latest version is the best way of protecting your device from being infected again in this manner. We also recommend enabling automatic updates if this option is available in order to help keep your device up to date.
For specific instructions on how to do this on your device, please refer to the manual that came with your NAS device or contact the manufacturer.
Change any ‘default’ passwords used by other devices
To best protect all the devices in your home from future security issues, we strongly recommend that you change the default passwords of any devices connected to your home network.
Devices that are commonly shipped with default passwords are internet connected appliances such as routers, Network Attached Storage (NAS) devices and CCTV systems.
For specific instructions on how to do this for these devices, please refer to the manual that came with the device or contact the manufacturer.
How do I know I’m now safe?
If you have followed the above advice & have rescanned your device and found it to be clean, you should have resolved the issue.
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
Virtual Network Computing Server notification
You may have received an email from us recently explaining that we’ve been notified of a device on your network that’s been configured as a Virtual Network Computing (VNC) server. This means the device can be accessed from outside your home network.
This notification is simply to make sure you’re aware of this and what it means. Once you’ve finished reading, you only need to take action if you think it’s needed.*
What has happened?
Virtual Network Computing is a screen sharing system that allows computers to be accessed remotely from another device on the internet.
For your safety, we work with a number of not-for-profit banking and security organisations that collect information on devices across the internet that appear to be misconfigured and/or at risk.
A device on your network has shown signs of running a Virtual Network Computing server exposed to the wider internet. By default, it doesn’t make use of encryption, meaning information being passed to and from your device could be accessed by a third party.
For more information on these reports please visit vncscan.shadowserver.org **
What can I do about it?
Choose the option below that best fits your situation:
1. I’ve configured a Virtual Network Computing server on my network on purpose
If you’ve purposely configured a Virtual Network Computing server on a device in your home, we suggest looking at alternative solutions that are encrypted to prevent information from being accessed.
This is because, while Virtual Network Computing does encrypt login credentials when accessing your server (such as your password), all information after logging in is passed across in plain-text. This means a malicious third party could access this data.
If you’re aware of the risks involved in using Virtual Networking Computing over the internet, or you’ve taken steps to ensure the traffic is encrypted, then you may decide no further action is required.
2. I’m not aware of a Virtual Network Computing server running on my home
It’s possible that Virtual Network Computing has been enabled on a device using your internet connection by default, or the setting has been switched on accidentally.
If you don’t need any of your devices to be accessible outside of your local network, then we recommend closing the ports that Virtual Network Computing uses in your Super Hub or router’s configuration. There are instructions below to guide you through this.
It’s worth noting that blocking this port will stop traffic leaving or entering your home network over this port only. Virtual Network Computing access within your home should continue to work as normal. All other services involving your home network will also remain unaffected by this change.
Ensure the VNC port is closed on your router’s firewall
Hub 3
To close the vulnerable port on the Virgin Media Hub:
- • Access your Hub's configuration page – default web address: 192.168.0.1
- • Log in with your username and password, shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep ports 5900 or 5800 open
- • Select the Port Triggering option
- • Remove any rules that will keep ports 5900 or 5800 open
Super Hub
To close the vulnerable port on the Hub 1.0/2.0’s firewall:
- • Access your Hub's configuration page – default web address: 192.168.0.1
- • Log in with your username and password, shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep ports 5900 or 5800 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep ports 5900 or 5800 open
- • Click the Apply option
Third party routers
If you use a third party router along with your Virgin Media Hub, your router's firewall will need to be configured to ensure ports 5900 and 5800 are not accessible outside of your local network. You can do this by blocking the port or removing any Port Forwarding rules for that port. To find out how, refer to the documents that came with your device or the manufacturer's website.
Ensure all devices on your network are protected by a firewall
It’s important to check all your devices are covered by a firewall. In most cases your firewall is configured as a part of your router – this is the case with the Virgin Media Hub. If you’ve disabled the firewall in your router, it’s crucial that you configure your devices to sit behind a firewall that is blocking ports 5900 and 5800. If this doesn’t apply to you, you can move onto the next step.
Modem Mode – If you’re using your Super Hub or Hub 3 in Modem Only mode, it’s essential that you’re using a firewall on any device or router that’s plugged directly into the Hub. That’s because when in Modem Only mode, your Hub doesn’t operate with a firewall. If this doesn’t apply to you, you can move onto the next step.
Demilitarized Zones (DMZ) – Most firewalls, including the one provided with the Super Hub and Hub 3 include a Demilitarized Zone option. This feature allows devices using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your firewall settings. Sometimes this is necessary if you’re using a device that has its own firewall configured.
If you have a device configured in your firewall's Demilitarized Zone that doesn’t use its own firewall, it’s crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider internet.
To check if a device is configured in the Demilitarized Zone on your Hub 3:
Access your Hub's configuration page – default web address: 192.168.0.1
Log in with your username and password, shown on the Hub itself
Select Security on the left side of the page
Select the DMZ option
To remove a device from the DMZ, tick the Disable box
To check if a device is configured in the Demilitarized Zone on your Virgin Media Hub 1.0 or 2.0:
Access your Hub's configuration page – default web address: 192.168.0.1
Log in with your username and password, shown on the Hub itself
Select Advanced Settings
Select DMZ
To remove a device from the DMZ, uncheck the tick box at the top of the page
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
SSDP Vulnerability alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a Simple Service Discovery Protocol (SSDP) vulnerability. If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
These fixes are provided as a courtesy and we are not responsible for any problems encountered whilst applying these steps and we are not able to provide any technical support for such problems.
Overview
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured.
The Simple Service Discovery Protocol (SSDP) is often used for discovery of Plug & Play (UPnP) devices on a local network. This is commonly used by streaming services and games consoles to be able to cast content between devices.
An SSDP vulnerability is a security issue whereby a 3rd party can use this protocol to gain unauthorized access to your network/devices for malicious purposes. If a 3rd party has access to your network/devices they will be able to perform a Distributed Denial of Service (DDoS) attack.
What has happened?
We suspect a device connected to your home network may have a Simple Service Discovery Protocol (SSDP) vulnerability.
For more information on these reports please visit ssdpscan.shadowserver.org*
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article. **
How can the issue be fixed?
Block external SSDP traffic
The easiest way to deal with SSDP vulnerabilities is to configure your firewall to block port 1900.
It is worth noting that blocking this port will only stop traffic over this port leaving or entering your home network. Services within your home that use this port should continue to work as normal
To close the vulnerable port on the Virgin Media Hub :
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep port 1900 open
- • Select the Port Triggering option
- • Remove any rules that will keep port 1900 open
To close the vulnerable port on the Hub 1.0/ 2.0’s firewall:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep port 1900 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep port 1900 open
- • Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub, your router's firewall will need to be configured to ensure port 1900 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for that port. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Ensure all devices on your network are protected by a firewall
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Hub. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that blocks ports 8080, 9040, 9050 & 3128. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured. If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
To check if a device is configured in the DMZ on your Virgin Media Hub :
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select the DMZ option
- • To remove a device from the DMZ, tick the Disable box
To check if a device is configured in the DMZ on your Virgin Hub 1.0 /2.0:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • To remove a device from the DMZ, uncheck the tick box at the top of the page
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
SNMP vulnerability alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as an open Simple Network Management Protocol (SNMP) vulnerability. If you have received this communication from us, please follow the advice given on this page to resolve the issue.
Overview
SNMP (Simple Network Management Protocol) is a method by which a device can be managed or accessed remotely on a computer network. An SNMP vulnerability is a security issue whereby a 3rd party can use this protocol to ultimately gain unauthorised access to your network/devices for malicious purposes, if the protocol is configured incorrectly.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have a SNMP vulnerability.
For more information on these reports please visit snmpscan.shadowserver.org **
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is important that you follow the advice in this article. *
How can the issue be fixed?
Block SNMP traffic
The easiest way to deal with SNMP threats/vulnerabilities is to configure your firewall to block UDP ports 161 and 162.
It is worth noting that blocking these ports will only stop traffic over that port leaving or entering your home network. Services within your home that use ports 161 and 162 should continue to work as normal.
To close the vulnerable port on the Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep ports 161 & 162 open
- • Select the Port Triggering option
- • Remove any rules that will keep ports 161 & 162 open
To ensure ports 161 & 162 are closed on the Hub 1.0 or 2.0’s firewall:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep ports 161 & 162 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep ports 161 & 162 open
- • Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub, your router's firewall will need to be configured to ensure ports 161 and 162 are not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for ports 161 and 162. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Ensure all devices on your network are protected by a firewall
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Hub. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that blocks ports 8080, 9040, 9050 & 3128. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured. If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
To check if a device is configured in the DMZ on your Virgin Media Hub :
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select the DMZ option
- • To remove a device from the DMZ, tick the Disable box
To check if a device is configured in the DMZ on your Virgin Hub 1.0 /2.0:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • To remove a device from the DMZ, uncheck the tick box at the top of the page
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
Remote Desktop Protocol server notification
You may have received an email from us recently explaining that we’ve been notified of a device on your network that’s been configured as a Remote Desktop Protocol (RDP) server. This means the device can be accessed from outside your home network.
This notification is simply to make sure you’re aware of this and what it means. Once you’ve finished reading, you only need to take action if you think it’s needed. *
What has happened?
Remote Desktop Protocol is a screen sharing system that allows computers to be accessed remotely from another device on the internet.
For your safety, we work with a number of not-for-profit banking and security organisations that collect information on devices across the internet that appear to be misconfigured and/or at risk.
A device on your network has shown signs of running a Remote Desktop Protocol server exposed to the wider internet. By default, older versions of the protocol don’t make use of encryption, meaning information being passed to and from your device could be accessed by a third party.
For more information on these reports please visit rdpscan.shadowserver.org *
What can I do about it?
Choose the option below that best fits your situation:
1. I’ve configured a Remote Desktop Protocol server on my network on purpose
If you’ve purposely configured a Remote Desktop Protocol server on a device in your home, we suggest ensuring it is updated to the latest version, which includes support for encryption. If you’re using the RDP server that comes with the Windows operating system, then updating Windows to the latest version will do this for you.
If you’re aware of the risks involved in using Remote Desktop Protocol over the internet, or you’ve taken steps to ensure the traffic is encrypted, then you may decide no further action is needed.
2. I’m not aware of a Remote Desktop Protocol server running on my home network
It’s possible that a Remote Desktop Protocol has been enabled on a device using your internet connection by default, or that the setting has been switched on accidentally.
If you don’t need any of your devices to be accessible outside of your local network, then we recommend closing the ports that Remote Desktop Protocol uses in your Super Hub or router’s configuration. There are instructions below to guide you through this.
It’s worth noting that blocking this port will stop traffic leaving or entering your home network over this port only. Remote Desktop Protocol access within your home should continue to work as normal. All other services involving your home network will also remain unaffected by this change.
Ensure the RDP port is closed on your router’s firewall
To close the vulnerable port on the Virgin Media Hub:
- • Access your Hub's configuration page – default web address: 192.168.0.1
- • Log in with your username and password, shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep port 3389 open
- • Select the Port Triggering option
- • Remove any rules that will keep port 3389 open
To close the vulnerable port on the Hub 1.0 or 2.0’s firewall:
- • Access your Hub's configuration page – default web address: 192.168.0.1
- • Log in with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep port 3389 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep port 3389 open
- • Click the Apply option
Third party routers
If you use a third party router along with your Virgin Media Hub, your router's firewall will need to be configured to ensure port 3389 is not accessible outside of your local network. This is done by blocking the port or removing any Port Forwarding rules. To find out how to do this, refer to the documents that came with your device or the manufacturer's website.
Ensure all devices on your network are protected by a firewall
It’s important to check all your devices are covered by a firewall. In most cases your firewall is configured as a part of your router – this is the case with the Virgin Media Hub. If you’ve disabled the firewall in your router, it’s crucial that you configure your devices to sit behind a firewall that’s blocking port 3389. If this doesn’t apply to you, you can move onto the next step.
Modem Mode – If you’re using your Hub in Modem Only mode, it’s essential that you’re using a firewall on any device or router that’s plugged directly into the Hub. That’s because when in Modem Only mode, your Hub doesn’t operate with a firewall. If this doesn’t apply to you, you can move onto the next step.
Demilitarized Zones (DMZ) – Most firewalls, including the one provided with the Virgin Media Hub include a Demilitarized Zone option. This feature allows devices using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your firewall settings. Sometimes this is necessary if you’re using a device that has its own firewall configured.
If you have a device configured in your firewall's Demilitarized Zone that doesn’t use its own firewall, it’s crucial you disable this option straight away. Computers operating without a firewall are extremely vulnerable to attack as all ports are exposed to the wider internet.
To check if a device is configured in the Demilitarized Zone on your Hub:
Access your Hub's configuration page – default web address: 192.168.0.1
Log in with your username and password, shown on the Hub itself
Select Security on the left side of the page
Select the DMZ option
To remove a device from the DMZ, tick the Disable box
To check if a device is configured in the Demilitarized Zone on your Virgin Media Hub 1.0 or 2.0:
Access your Hub's configuration page – default web address: 192.168.0.1
Log in with your username and password, shown on the Hub itself
Select Advanced Settings
Select DMZ
To remove a device from the DMZ, uncheck the tick box at the top of the page.
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
Receiving An Open TFTP Vulnerability alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as an open TFTP vulnerability. If you have received this communication from us, please follow the advice given on this page to resolve the issue.
Overview
TFTP is a service that allows for other devices on a network to remotely access files and folders on a device running the service without entering in login credentials. This service is designed only to be used on a small local network, such as your home, but when exposed to the wider Internet it can be misused by third parties to commit abuse.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have an open TFTP vulnerability. For more information on these reports please visit tftpscan.shadowserver.org*
If the settings are left open they can be exploited to steal personal information and unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article. **
How can the issue be fixed?
An open TFTP vulnerability can be resolved by configuring your firewall to block UDP port 69.
It is worth noting that blocking this port will only stop traffic over this port leaving or entering your home network. Services within your home that use this port should continue to work as normal.
To configure port blocking on the Virgin Media Hub:
1. Log into the Settings page of the Super Hub. For details how to do this see Configure Advanced Settings on your Virgin Media Hub
2. Select Advanced Settings
3. Select Firewall
4. Ensure the Firewall is ticked and Firewall Protection is set to Medium
Alternatively:
To ensure port 123 is closed on the Super Hub 1 or 2’s firewall:
1. Access your Hub's configuration page - default web address: 192.168.0.1
2. Login with your username and password, default will be shown on the Hub itself
3. Select Advanced Settings and accept the prompt
4. Scroll down to the Security section
5. Select the Port Forwarding option
6. Tick the Delete box next to any rules that will keep port 123 open
7. Click the Apply option
8. Select the Port Triggering option
9. Tick the Delete box next to any rules that will keep port 123 open
10. Click the Apply option
To close the vulnerable port(s) on the Virgin Media Hub
1. Access your Hub's configuration page - default web address: 192.168.0.1
2. Login with your username and password, default will be shown on the Hub itself
3. Select Security on the left side of the page
4. Select the Port Forwarding option
5. Remove any rules that will keep port 123 open
6. Select the Port Triggering option
7. Remove any rules that will keep port 123 open
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub your router's firewall will need to be configured to ensure port 123 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for port 123. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website
Make sure all devices on your network are protected by a firewall
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Hub. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that blocks ports 8080, 9040, 9050 & 3128. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured. If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
To check if a device is configured in the DMZ on your Virgin Media Hub :
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select the DMZ option
- • To remove a device from the DMZ, tick the Disable box
To check if a device is configured in the DMZ on your Virgin Hub 1.0 /2.0:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • To remove a device from the DMZ, uncheck the tick box at the top of the page.
What is an Open Proxy alert?
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified of an Open Proxy server running on your Internet connection. This can allow malicious third parties to use your Broadband connection in order to mask their own online identity when committing abusive acts, such as sending spam email or participating in hacking activity.
If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
It would appear there is an Open Proxy server running on your Internet connection. You're probably not aware that your Internet connection is allowing external traffic to pass through it, which means a device on your home network may be infected with malware or you may have misconfigured remote access software installed.
It is therefore important that you follow the advice in this article*.
How can the issue be fixed?
You should follow the advice listed in the options below:
I have not set up any proxy servers on my home network
1. Check your devices for malware
A device on your network may have been configured by a malicious third party as a result of a malware infection on the affected device.
The easiest way to do this is by using an online virus scanner; some suggested sites are;
• Virgin Media Internet Security**
• eset.com/int/home/online-scanner**
If you are using an Android or iOS device, you can find a variety of virus scanners on the Google Play Store or App Store.
If an infection has been identified, use your internet security package to remove it.
If you have an existing security package installed, please read the instructions on how to remove infections from your device.
If you have an existing security package installed, please consult the instructions on how to remove infections from your device.
If you don't have an existing security package, Sign into your My Virgin Media account and register for Virgin Media Internet Security to start your 3-month trial today.
No bank or credit card details are needed upfront for the trial.
Once downloaded and installed it will immediately run a scan of your device.
If you already use Virgin Media Internet Security, make sure "Viruses and spyware scanning" is turned on.
2. Remove any unwanted applications
Check the applications installed on all of your devices, if there are any programs that are no longer required or have been installed without your knowledge, uninstall it. Pay close attention to any ‘Remote Access’ or ‘Proxy’ applications, if you don’t need it, it would be wise to remove it.
The method for listing the applications installed on your device as well as removing it varies between devices and operating systems, for details on how to do this refer to your device’s manual.
3. Seek advice from a computer engineer if the issue has not been identified
If you have been unable to identify any unwanted applications or malware infections responsible for running an open proxy server on your device without your knowledge, we recommend you consult an IT professional such as a computer engineer for further support. This is because more drastic action may be required – such as restoring your device to factory defaults.
If you have configured a device on my network to act as a proxy server
If you have knowingly configured a proxy server in your home, it is important you follow the below steps to ensure the service is not vulnerable.
1. Setup authentication on your proxy server
If you require access to your proxy server from devices outside of your home network, it is essential that your server is configured to require authentication from anyone who attempts to connect to it. This will mean only users with the correct login credentials for your proxy server will be able to use it.
Most proxy servers programs will allow authentication to be configured in the software’s control panel or configuration file. For instructions specific to the proxy software running on your server, please refer the application’s official user documentation.
2. Block external proxy access if you do not require it
If you do not require access to your proxy server from outside your home network, we recommend you block the ports your proxy server software uses in your router’s firewall.
Common ports used by proxy servers include TCP & UDP ports 8080, 9040, 9050, 3128.
If you are unsure what port(s) your proxy server is configured to use, please refer to your server’s proxy configuration file or the server software’s manual.
To configure port blocking on a Virgin Media provided Hub:
To close the vulnerable ports on the Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep ports you do not require open
- • Select the Port Triggering option
- • Remove any rules that will keep ports you do not require open
To close the vulnerable ports on the Hub 1.0 or 2.0:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep any not required ports open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep any not required ports open
- • Click the Apply option
Ensure all devices on your network are protected by a firewall
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Hub. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that blocks ports 8080, 9040, 9050 & 3128. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured. If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
To check if a device is configured in the DMZ on your Virgin Media Hub :
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select the DMZ option
- • To remove a device from the DMZ, tick the Disable box
To check if a device is configured in the DMZ on your Virgin Hub 1.0/2.0:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • To remove a device from the DMZ, uncheck the tick box at the top of the page
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
What is the Open Portmapper Vulnerability?
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as an Open Portmapper vulnerability. If you have received such a communication from us, please follow the advice given on this page to help resolve the issue.
Overview
There is a design flaw that exists in the Portmapper service currently in use on a device on your home network. Portmapper, also known as RPC Bind or RPC Portmap, is a service used by computer systems to assist with networking tasks.
This flaw can allow remote 3rd party attackers to gain unauthorised access and perform Distributed Denial of Service (DDoS) attacks against target machines. A remote attacker can leverage this flaw by sending a specially crafted request to an affected Portmapper server.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have an open Portmapper vulnerability.
For more information on these reports please visit portmapperscan.shadowserver.org*
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is important that you follow the advice in this article. **
How can the issue be fixed?
Block external Portmapper traffic
The easiest way to deal with an open Portmapper vulnerability is to configure your firewall to block UDP port 111.
It is worth noting that blocking this port will only stop traffic over this port leaving or entering your home network. Services within your home that use this port should continue to work as normal.
To close the vulnerable port on the Virgin Media Hub :
- • Access the Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep port 111 open
- • Select the Port Triggering option
- • Remove any rules that will keep port 111 open
Virgin Media Hub
To close the vulnerable port on the Hub 1.o or 2.o’s firewall:
- • Access the Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep port 111 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep port 111 open
- • Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub, the router's firewall will need to be configured to ensure port 111 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for that port. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Ensure all devices on your network are protected by a firewall
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Hub. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that is blocking port 53. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured.
If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
Receiving an Open Memcached Vulnerability alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has an open Memcached vulnerability. If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
Memcached is a distributed memory object caching system, often used in conjunction with web servers in order to alleviate database load. When configured incorrectly it can be accessed by unauthorised third parties, who may be able to access the data stored on the server as well as commit abusive acts.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have an open Memcached vulnerability.
For more information on these reports please visi memcachedscan.shadowserver.org *
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example, a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article.**
How can the issue be fixed?
Block external Memcached traffic
An open Memcached vulnerability can be resolved by configuring your firewall to block the port the server is configured to use, in most cases this is UDP/TCP port 11211.
It is worth noting that blocking this port will only stop traffic over this port leaving or entering your home network. Services within your home that use this port should continue to work as normal.
To close the vulnerable port on the Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep port 11211 open
- • Select the Port Triggering option
- • Remove any rules that will keep port 11211 open
To close the vulnerable port on the Super Hub 1.0 or 2.0’s firewall:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep port 11211 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep port 11211 open
- • Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub, your router's firewall will need to be configured to ensure port 11211 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for port 11211. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Ensure all devices on your network are protected by a firewall
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Hub. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that is blocking port 11211. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured.
If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
How do I know I’m now safe?
If you have followed the above advice you can be confident that you have resolved the issue.
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide technical support for these issues.
Open DNS resolver vulnerability alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as an Open DNS Resolver. If you have received such a communication from us, read the advice given on this page to help resolve the issue. Note: This article is intended to provide advice. Virgin Media is not responsible for any issues encountered in the course of resolving the issue and is not able to provide any technical support for such problems.
Overview
The Domain Name System (DNS) is a system used by computers to convert domain names to an IP address on the Internet. A DNS server is a system that accepts requests from other computer systems to convert domains to IP addresses.
An open recursive DNS Resolver is a DNS server that has been opened up to answer DNS queries from any computer system on the Internet. If configured incorrectly, these servers can be exploited to unwittingly participate in malicious activities.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have an open DNS resolver vulnerability.
For more information on these reports please visit dnsscan.shadowserver.org*
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is important that you follow the advice in this article. **
Closing the vulnerable port
The easiest way to deal with an open DNS resolver is to configure your firewall to block port 53 to prevent DNS queries from outside your home network.
If you have a specific need to have a DNS resolver that answers to queries from the Internet, please ensure your server is configured to only accept traffic from IP addresses that need to use the server.
Hub 3
To close the vulnerable port on the Virgin Media Hub:
• Access your Hub's configuration page - default web address: 192.168.0.1
• Login with your username and password, default will be shown on the Hub itself.
• Select Security on the left side of the page
• Select the Port Forwarding option
• Remove any rules that will keep port 53 open
• Select the Port Triggering option<
• Remove any rules that will keep port 53 open
To close the vulnerable port on the Virgin Media Hub 1.o or 2.0’s firewall:
• Access your Hub's configuration page - default web address: 192.168.0.1
• Login with your username and password, default will be shown on the Hub itself
• Select Advanced Settings and accept the prompt
• Scroll down to the Security section
• Select the Port Forwarding option
• Tick the Delete box next to any rules that will keep port 53 open
• Click the Apply option
• Select the Port Triggering option
• Tick the Delete box next to any rules that will keep port 53 open
• Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub, your router's firewall will need to be configured to ensure port 53 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for port 53. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Check devices are protected by a firewall
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Hub. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that is blocking port 53. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Super Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Super Hub and Hub 3 include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured.
If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide any technical support for these issues.
Receiving an NTP Monlist Vulnerability Alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as a Network Time Protocol Monlist vulnerability (NTP Monlist). If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
There exists a design flaw in NTP servers that can allow attackers to perform Distributed Denial of Service (DDoS) attacks against target machines. A remote attacker can leverage this flaw by sending a specially crafted request to an affected NTP server.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have an NTP monlist vulnerability.
For more information on these reports please visit ntpmonitorscan.shadowserver.org *
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article. **
What can I do about it?
You can run the following command to check your server for the NTP Mode 6 & open NTP monlist vulnerabilities:
ntpq -c rv [IP]
If you see a response, your server may be used in attacks.
Once you have identified the source of any issue within your home, you should upgrade to NTP-4.2.7p26 or later.
To resolve this vulnerability we would request that you check your router settings and all of your devices to ensure that TCP/UDP port 123 (NTP) is closed. The precise method for doing this will depend upon your make, model and operating system of your device.
Block NTP traffic
The easiest way to deal with the NTP vulnerability is to configure your firewall to block port 123.
It is worth noting that blocking this port will only stop traffic over that port leaving or entering your home network. Services within your home that use port 123 should continue to work as normal.
You can block NTP traffic yourself by following the instructions below:
- • Configure your router firewall to block UDP port 123
- • Disable NTP over TCP/IP on any remotely accessible devices
To configure port blocking on the Virgin Media Hub:
1. Log into the Settings page of the Super Hub. For details how to do this see Configure Advanced Settings on your Virgin Media Hub
2. Select Advanced Settings
3. Select Firewall
4. Ensure the Firewall is ticked and Firewall Protection is set to Medium
Alternatively:
To ensure port 123 is closed on the Super Hub 1 or 2’s firewall:
1. Access your Hub's configuration page - default web address: 192.168.0.1
2. Login with your username and password, default will be shown on the Hub itself
3. Select Advanced Settings and accept the prompt
4. Scroll down to the Security section
5. Select the Port Forwarding option
6. Tick the Delete box next to any rules that will keep port 123 open
7. Click the Apply option
8. Select the Port Triggering option
9. Tick the Delete box next to any rules that will keep port 123 open
10. Click the Apply option
To close the vulnerable port(s) on the Virgin Media Hub
1. Access your Hub's configuration page - default web address: 192.168.0.1
2. Login with your username and password, default will be shown on the Hub itself
3. Select Security on the left side of the page
4. Select the Port Forwarding option
5. Remove any rules that will keep port 123 open
6. Select the Port Triggering option
7. Remove any rules that will keep port 123 open
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub your router's firewall will need to be configured to ensure port 123 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for port 123. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website
Demilitarized Zone (DMZ)
Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured. If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
To check if a device is configured in the DMZ on your Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings
- • Select DMZ
- • To remove a device from the DMZ, uncheck the tick box at the top of the page
To check if a device is configured in the DMZ on your Virgin Media Hub 1.0/2.0:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select 'Security' on the left side of the page
- • Select the 'DMZ' option
- • To remove a device from the DMZ, tick the 'Disable' box
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide any technical support for these issues.
Receiving a NTP Mode 6 Vulnerability alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as a Network Time Protocol Mode 6 vulnerability (NTP Mode 6). If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
There exists a design flaw in NTP servers that can allow attackers to perform Distributed Denial of Service (DDoS) attacks against target machines. A remote attacker can leverage this flaw by sending a specially crafted request to an affected NTP server.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured.
We suspect a device connected to your home network may have an NTP mode 6 vulnerability.
For more information on these reports please visit ntpscan.shadowserver.org *
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is important that you follow the advice in this article.**
What can I do about it?
You can run the following command to check your server for the NTP Mode 6 & open NTP monlist vulnerabilities:
ntpq -c rv [IP]
If you see a response, your server may be used in attacks.
Once you have identified the source of any issue within your home, you should upgrade to NTP-4.2.7p26 or later. **
To resolve this vulnerability we would request that you check your router settings and all of your devices to ensure that TCP/UDP port 123 (NTP) is closed. The precise method for doing this will depend upon your make, model and operating system of your device.
Block NTP traffic
The easiest way to deal with the NTP vulnerability is to configure your firewall to block port 123.
It is worth noting that blocking this port will only stop traffic over that port leaving or entering your home network. Services within your home that use port 123 should continue to work as normal.
You can block NTP traffic yourself by following the instructions below:
- • Configure your router firewall to block UDP port 123
- • Disable NTP over TCP/IP on any remotely accessible devices
To configure port blocking on the Virgin Media Hub:
1. Log into the Settings page of the Super Hub. For details how to do this see Configure Advanced Settings on your Virgin Media Hub
2. Select Advanced Settings
3. Select Firewall
4. Ensure the Firewall is ticked and Firewall Protection is set to Medium
Alternatively:
To ensure port 123 is closed on the Super Hub 1 or 2’s firewall:
1. Access your Hub's configuration page - default web address: 192.168.0.1
2. Login with your username and password, default will be shown on the Hub itself
3. Select Advanced Settings and accept the prompt
4. Scroll down to the Security section
5. Select the Port Forwarding option
6. Tick the Delete box next to any rules that will keep port 123 open
7. Click the Apply option
8. Select the Port Triggering option
9. Tick the Delete box next to any rules that will keep port 123 open
10. Click the Apply option
To close the vulnerable port(s) on the Virgin Media Hub
1. Access your Hub's configuration page - default web address: 192.168.0.1
2. Login with your username and password, default will be shown on the Hub itself
3. Select Security on the left side of the page
4. Select the Port Forwarding option
5. Remove any rules that will keep port 123 open
6. Select the Port Triggering option
7. Remove any rules that will keep port 123 open
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub your router's firewall will need to be configured to ensure port 123 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for port 123. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website
Demilitarized Zone (DMZ)
Most firewalls, including the one provided with the Virgin Media Hub include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured. If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
To check if a device is configured in the DMZ on your Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings
- • Select DMZ
- • To remove a device from the DMZ, uncheck the tick box at the top of the page
To check if a device is configured in the DMZ on your Virgin Media Hub 1.0/2.0:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select 'Security' on the left side of the page
- • Select the 'DMZ' option
- • To remove a device from the DMZ, tick the 'Disable' box
*Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide any technical support for these issues.
Network Attacks Alert
You might have received a letter and/or email from Virgin Media to explain that we’ve been notified of malicious traffic originating from a device that uses your home broadband connection. If you've heard from us about this, there’s no need to worry. The advice on this page should help sort things out.
Why have you written to me?
We believe a device in your home has been infected with malware that’s sending malicious traffic to other computer systems, and could be trying to access them without authorisation. We take these attacks very seriously, so when we think a customer of ours might have had an infected device, we send them an alert with advice on what to do next.
What has happened?
We’ve received a report that suggests malicious traffic is originating from a device on your home network. We realise this is unlikely to be your fault, but this kind of abuse is against our Acceptable Use Policy. If the abuse continues we might have to suspend or cancel your broadband service.
It is therefore important that you follow the advice in this article. *
What can I do about it?
We’re here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure your home network. Please apply these steps in order:
1. Check to see if your device has an infection
The easiest way to do this is by using an online virus scanner; some example sites are;
If you are using an Android or iOS device, you can find a variety of virus scanners on your device’s app store.
2. Use your internet security package to remove any infections
If you have an existing security package installed, please read the instructions on how to remove infections from your device.
If you don't have an existing security package, Sign into your My Virgin Media account and register for Virgin Media Internet Security to start your 3-month trial today.
No bank or credit card details are needed up front for the trial.***
Once downloaded and installed it will immediately run a scan of your device.
If you already use Virgin Media Internet Security, make sure "Viruses and spyware scanning" is turned on.
3. Change the passwords for all of your accounts
Once the malware has been removed, you should change the passwords for all the online and email accounts you use.
If any of your passwords were obtained by a malicious third party as a result of the malware infection, it is highly likely they attempted or will attempt to use the same passwords across as many websites and online services as possible, in the hope that the same passwords is used for other accounts you use online.
When changing your passwords, it is important that you use different passwords for all your online accounts and pick strong passwords that are difficult to guess.
4. Get up-to-date software
Keep your operating system and application software up-to-date. Install software patches so that attackers can't take advantage of known problems or vulnerabilities. Many operating systems offer automatic updates. If this option is available, you should enable it.
5. Activate Web Safe
In order to avoid future infections on your home network it is recommended that you turn on Virus Safe, which is available as part of our free Web Safe service which can be found within My Virgin Media. Web Safe will help you block access to web sites known to be infected or to distribute Malware. To access Web Safe just sign in to your account at virginmedia.ie/sign-in and select My Apps.
6. Check your contact email address
It is important to provide an up to date contact email address to enable us to advise you of any significant issues that may affect the use of your Virgin Media services. To update your contact email address, simply sign in to your account at virginmedia.ie/sign-in and select My Profile.
7. Check Auto Forward setting in Virgin Media Mail
In addition, it’s important that you check your mail forwarding rules to ensure that your emails aren’t being forwarded without your knowledge.
To check this in Virgin Media Mail webmail:
- • Go to https://www.virginmedia.ie/webmail/
- • Sign in using your My Virgin Media username and password
- • Click the System Menu icon on the right side of the menu bar and then click the Settings menu item
- • Select the Auto Forward tab
This will display email addresses set to receive forwarded emails from your Virgin Media mailbox. If there is an email address you don’t recognise, and which you didn’t intend to forward your email to, then please select it and delete the forwarding rule.
**Any links to external sites are provided as a courtesy and we are not responsible for the content of these sites or problems encountered while applying their advice. Unfortunately we're not able to provide any technical support for these issues.
Receiving a Netbios Vulnerability alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as an open NetBIOS. If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
NetBIOS is used to share files and folders across a local network. Other applications can use NetBIOS to map a network, allowing them to send messages to destination computers. Ports commonly used by NetBIOS can be exploited to commit abuse when exposed to the wider Internet.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have an open NetBIOS vulnerability.
For more information on these reports please visit netbiosscan.shadowserver.org*
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article. **
What can I do about it?
We're here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure home network.
To resolve this issue, please follow the steps below.
Block NetBIOS traffic:
Virgin Media Hub
To close the vulnerable port on the Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep ports 135, 137 & 139 open
- • Select the Port Triggering option
- • Remove any rules that will keep ports 135, 137 & 139 open
To close the vulnerable port on the Hub 1.0/2.0:’s firewall:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Remove any rules that will keep ports 135, 137 & 139 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep ports 135, 137 & 139 open
- • Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub, your router's firewall will need to be configured to ensure ports 135, 137 and 139 are not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for that port. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Links to external sites are provided as a courtesy and we are not responsible for the content of these sites or any problems encountered while applying their advice. Unfortunately we're not able to provide any technical support for these issues.
What is the Multicast DNS vulnerability alert?
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that a device on your network has a vulnerability known as an open Multicast DNS. If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
Multicast DNS is used to resolve host names to IP address on a small computer network. It is commonly used to share music and video streaming services between devices on your home network. When exposed to the wider Internet, it can be misused by 3rd parties in order to commit abuse.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised or misconfigured. This means that your compromised or misconfigured device is publicly accessible on the Internet, and therefore the scanning that is performed by these organisations is not within your private network.
We suspect a device connected to your home network may have an open Multicast DNS vulnerability.
For more information on these reports please visit mdns.shadowserver.org*
If the settings are left open they can be exploited to unwittingly participate in malicious activities, for example, a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article. **
How can the issue be fixed?
Block Multicast DNS traffic
The easiest way to deal with a Multicast DNS vulnerability is to configure your firewall to block port 5353.
It is worth noting that blocking this port will only stop traffic over that port leaving or entering your home network. Services within your home that use port 5353 should continue to work as normal.
Hub
To close the vulnerable port on the Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep port 5353 open
- • Select the Port Triggering option
- • Remove any rules that will keep port 5353 open
To close the vulnerable port on the Hub 1.o or 2.0’s firewall:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep port 5353 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep port 5353 open
- • Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Virgin Media Hub, your router's firewall will need to be configured to ensure port 5353 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for port 5353. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Ensure devices are firewall protected
It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router, this is the case with the Virgin Media Super Hub and Hub 3. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that is blocking port 5353. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Super Hub or Hub 3 in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Virgin Media Super Hub and Hub 3 include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured.
If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
Mirai malware alert
You may have recently received a letter and/or email from Virgin Media explaining we have been notified that an online device on your network contains malware named Mirai. If you have received this communication from us, please follow the advice given on this page to resolve the issue.
Overview
Mirai is a form of malware that specifically targets Internet-connect appliances that are connected to your network. These are often called ‘Internet of Things’ devices. These devices can be CCTV systems, smart TVs, smart plugs, NAS (Network Attatched Storage) drives etc.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that are infected with malware. They have notified us that a device on your home Internet connection (or one connected to your home network) is infected with malware.
We are unable to specify exactly what device in your home is infected, but it is likely to be a ‘smart’ device such as a CCTV camera or Network Attached Storage (NAS) drive rather than a traditional computer or laptop.
If the malware is not removed, the device can be exploited to unwittingly participate in malicious activities, for example a Distributed Denial of Service (DDoS) attack.
It is therefore important that you follow the advice in this article*.
How can the issue be fixed?
We’re here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure your home network. Make sure you follow these steps in order.
Secure Remote Access to your devices
The Mirai malware targets devices that use the Telnet remote access protocol and still use the default username and password set by its manufacturer. These default credentials are often widely available on the Internet, which can allow 3rd parties to remotely access the device and install malware on it.
To secure Telnet access on your devices, please follow one of the below steps:
Change default passwords
Internet-connected appliances often utilise a default username and password that the manufacturer has set for the Telnet service. These are often the same across hundreds if not thousands of devices from that manufacturer.
Changing the password to your own custom password will protect you against your device from being targeted by Mirai in the future, as the malware uses a list of common device passwords to connect to your device through Telnet.
Make sure to disconnect the device from the Internet before changing the passwords.
Steps on how to change the Telnet password used by any Internet-connected appliances on your home network vary between devices and manufacturers. Consult the documentation that came with your device for details on how to do this.
Disable Telnet access if it isn’t required
If you do not need the Telnet service to be used by systems outside of your home network, it is highly recommended that you block it so only devices within your home can use it.
The Telnet service does not use encryption, meaning any passwords you send between devices using Telnet are sent across in plain text – this poses a security risk.
Only action this step if you are certain you do not need the Telnet service to be accessible from outside your home network.
Hub
To close the port used by Telnet on the Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the Port Forwarding option
- • Remove any rules that will keep port 23 open
- • Select the Port Triggering option
- • Remove any rules that will keep port 23 open
Hub 1.0/2.0
To close the port used by Telnet on your Virgin Media Hub 1 or 2’s firewall:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings and accept the prompt
- • Scroll down to the Security section
- • Select the Port Forwarding option
- • Tick the Delete box next to any rules that will keep port 23 open
- • Click the Apply option
- • Select the Port Triggering option
- • Tick the Delete box next to any rules that will keep port 23 open
- • Click the Apply option
3rd party routers
If you use a 3rd party router in conjunction with the Hub 3 or Super Hub 1, 2 or 2ac, your router's firewall will need to be configured to ensure port 23 is not accessible outside of your local network - this can be performed by blocking the port or removing any Port Forwarding rules for that port. In order to identify how to do this with your particular router, refer to the documentation for your device or refer to the manufacturer's website.
Remove the Mirai infection
Once the Telnet service has been secured using one of the solutions above, the next step is to remove the Mirai infection from your device(s).
To do this follow the below steps in order:
- • Disconnect the device from the network
- • While disconnected from the network, perform a reboot. The Mirai malware exists in dynamic memory so rebooting the device will clear the malware
- • You should reconnect to the network only after rebooting and changing the password. If you reconnect before changing the password, the device could be quickly re-infected with the Mirai malware
If you have followed the steps above but continue to get notifications regarding this security issue, please follow the below steps:
Firewall - It is important to check all your devices sit behind a firewall. In most cases your firewall is configured as a part of your router. If you have specifically disabled the Firewall in your router, it is crucial that you configure your devices to sit behind a firewall that is blocking port 23. If this does not apply to you, please proceed to the next step.
Modem Mode - If you are using your Virgin Media Hub in Modem Only mode, it is essential that you are using a firewall on any device or router that is plugged directly into the Hub. When in Modem Only mode, your Hub does not operate with a firewall. If this does not apply to you, please proceed to the next step.
DMZ - Most firewalls, including the one provided with the Hub 3 and Super Hub 1, 2 or 2ac include a DMZ option. This feature allows for a device using a specific local IP address on your home network (e.g. 192.168.0.2) to bypass your Firewall settings. This is occasionally necessary if you are using a device that has its own firewall configured. If you have a device configured in your firewall's DMZ that does not use its own firewall, it is crucial that you disable this option immediately. Computers operating without a firewall are extremely vulnerable to attack as all ports are essentially exposed to the wider Internet.
To check if a device is configured in the DMZ on your Hub 3:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Security on the left side of the page
- • Select the DMZ option
- • To remove a device from the DMZ, tick the Disable box
To check if a device is configured in the DMZ on your Virgin Media Hub:
- • Access your Hub's configuration page - default web address: 192.168.0.1
- • Login with your username and password, default will be shown on the Hub itself
- • Select Advanced Settings
- • Select DMZ
- • To remove a device from the DMZ, uncheck the tick box at the top of the page
How do I know I’m now safe?
If you have followed the above advice you can be confident that you have resolved the issue.
What is a malware alert?
You may have recently received a letter or email from Virgin Media explaining that we have been notified that a device on your network contains malware. If you've received this communication from us, please follow the advice given below to resolve the issue.
Overview
When we suspect that a customer has become infected with malware, we will send them an alert giving an overview of the malware infection and advice on what to do next.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that are infected with malware. They have notified us that a device on your home Internet connection (or one connected to your home network) is infected with malware.
Your financial transactions and personal data could be at risk, so it is important that you follow the advice in this article. *
Want to fix the issue yourself?
We’re here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure your home network.
1. Check to see if your device has an infection
The easiest way to do this is by using an online virus scanner; some suggested sites are;
If you are using an Android or iOS device, you can find a variety of virus scanners on your device’s app store.
2. Use your internet security package to remove any infections
If you have an existing security package installed, please consult the instructions on how to remove infections from your device.
If you don't have an existing security package, Sign into your My Virgin Media account and register for Virgin Media Internet Security to start your 3-month trial today.
No bank or credit card details are needed upfront for the trial.
Once downloaded and installed it will immediately run a scan of your device.
If you already use Virgin Media Internet Security, make sure 'Viruses and spyware scanning' is turned on.
3. Change the passwords for all of your accounts
Once the malware has been removed, you should change the passwords for all the online and email accounts you use.
If any of your passwords were obtained by a malicious third party as a result of the malware infection, it is highly likely they attempted or will attempt to use the same passwords across as many websites and online services as possible, in the hope that the same password is used for other accounts you use online.
When changing your passwords, it is important that you use different passwords for all your online accounts and pick strong passwords that are difficult to guess.
4. Get up-to-date software
5. Activate Web Safe
In order to avoid future infections on your home network it is recommended that you turn on Virus Safe, which is available as part of our free Web Safe service which can be found within My Virgin Media. Web Safe will help you block access to web sites known to be infected or to distribute malware. To access Web Safe just sign in to your account at virginmedia.ie/onlinearmour
6. Check your contact email address
It is important to provide an up to date contact email address to enable us to advise you of any significant issues that may affect the use of your Virgin Media services. To update your contact email address simply sign in to your account at virginmedia.ie/onlinearmour and select My Profile.
7. Check Auto Forward setting in Virgin Media Mail
In addition, it’s important that you check your mail forwarding rules to ensure that your emails aren’t being forwarded without your knowledge.
To check this in Virgin Media Mail webmail:
- • Go to https://www.virginmedia.ie/webmail/
- • Sign in using your My Virgin Media username and password
- • Click the System Menu icon on the right side of the menu bar and then click the Settings menu item
- • Select the Auto Forward tab
This will display email addresses set to receive forwarded emails from your Virgin Media mailbox. If there is an email address you don’t recognise, and which you didn’t intend to forward your email to, then please select it and delete the forwarding rule.
8. How do I know I’m now safe?
If you have followed the above advice and have rescanned your device and found it to be clean, you should have resolved the issue.
Locked Virgin Media account alert
My Virgin Media email account has been locked
We’ve been alerted that your Virgin Media Mail account may have been used to send spam* emails. This may have been caused by unintentionally accessing a website or opening an email link.
As we take security seriously, we've temporarily blocked access to them and made sure no changes can be made to the accounts.
Don’t worry, it’s really easy to get everything back to normal. You don’t even have to pick up the phone.
Firstly, you will need to create a new email password online. Before you do this, please follow the advice below for security reasons.
- Do not use existing or previous passwords
- Choose one between 8-10 characters that includes numbers, uppercase and lowercase letters
- Avoid using complete words
These steps make it much harder for hackers to guess your password.
If you’re ready to create your new password, simply head over to My Virgin Media:
- • Click Sign In
- • Select Forgotten your email or password? under the password box
- • Follow the instructions to change your password
• Once your password's reset, make sure your emails are not being forwarded without your knowledge.
- • Go to https://www.virginmedia.ie/webmail/
- • Sign in with your username and password
- • Click on Menu (top right) and then, Settings
- • Expand the Email option
- • Select Auto Forward
This will show any email addresses set to receive forwarded emails from your Virgin Media mailbox. If it shows one you don’t recognise, select and delete the forwarding rule.
Virgin Media takes your security very seriously. That’s why we always want our customers to know what’s happening as soon as an issue is detected. It’s our policy to proactively advise customers of external security threats which may affect them in the ever-changing digital world.
Compromised mailbox alert
You’ll see a compromised mailbox alert if we suspect a third party is using one or more of your Virgin Media email addresses to send spam or junk emails. This article gives advice on how to fix the issue. *
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that appear to be compromised and sending spam or junk mails.
It's probable that the person or organisation sending these emails obtained your username and password from a computer or device you've used which has potentially been infected with a virus or malware.
This could be a computer or device such as a tablet used inside or outside your home.
How can the issue be fixed?
We're here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure your mailbox and home network. Please apply these steps in order:
1. Check your devices for Malware
The easiest way to do this is by using an online virus scanner; some suggested sites are;
If you are using an Android or iOS device, you can find a variety of virus scanners on the App Store.
Should all anti-virus scans come back as clean, it is possible that the unauthorised third party is using a username and password that you may have used somewhere else on the Internet, and they’ve attempted to login to your Virgin Media mail account to see if the same username and password are in use for your email. Ensuring you have a completely unique password for your Virgin Media mail account will ensure this doesn’t happen again.
2. Secure your email account
Once you’ve ensured that your devices are free from infection, you should change your My Virgin Media password and security question to block any potential unauthorised access to your Virgin Media email address.
Sign in to My Virgin Media. Remember your username may not be the same as your Virgin Media Mail email address.
Change your password to by clicking the My Profile tab and selecting Change Password. Please make sure you don't use the same password on other online sites you login to such as Facebook or Amazon.
Please see How to choose a strong and secure password for tips on choosing a new password. We recommend using the maximum 10 characters for your new password.
Then update your security details by choosing a new Security question and answer. This will prevent anyone resetting your password without your knowledge.
If you use an email program on your device you’ll need to enter your new email password next time you check your Virgin Media email.
3. Check your contact email address
It is important to provide an up to date contact email address to enable us to advise you of any significant issues that may affect the use of your Virgin Media services. To update your contact email address simply sign in to My Virgin Media and select My Profile.
4. Check Auto Forward settings in Virgin Media Mail
In addition, it’s important that you check your mail forwarding rules to ensure that your emails aren’t being forwarded without your knowledge.
- • Go to mail.virginmedia.com
- • Sign in using your My Virgin Media username and password
- • Click the System menu icon Settings on the right side of the menu bar and then click the Settings menu item
- • Expand the Email option
- • Select Auto Forward
This will display email addresses set to receive forwarded emails from your Virgin Media mailbox. If there is an email address you don’t recognise, and which you didn’t intend to forward your email to, then please select it and delete the forwarding rule.
Receiving a Ghost Push Malware alert
You may have recently received a letter and/or email from Virgin Media explaining that we have been notified that an Android device on your network contains malware named Ghost Push. If you have received such a communication from us, please follow the advice given on this page to resolve the issue.
Overview
Ghost Push is a form of Trojan that specifically targets the Android operating system. The malware is mainly distributed through applications downloaded from untrusted third parties, but can also be hidden in applications downloaded from official markets such as Google Play.
What has happened?
We work with a number of not-for-profit organisations across the banking industry and security sectors that collate information on devices across the Internet that are infected with malware. They have notified us that an Android device on your home Internet connection (or one connected to your home network) is infected with malware.
Your financial transactions and personal data could be at risk. It is therefore important that you follow the advice in this article.*
Want to fix the issue yourself?
We’re here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure your home network.
Please apply these steps in order:
1 - Check to see if your device has an infection
The easiest way to do this is by using an anti-virus scanner; some suggested are;
- Virgin Media Internet Security
You can find these and other virus scanners on the Google Play Store.
Check Point, a threat research and security insights blog, provides a website where it’s possible to check if your Google account has been affected by Gooligan:
2 - Restore to Factory settings
If it is found that your device has the Ghost Push malware, the only method to completely clear your device of the infection is to restore to factory settings. However, it is very important to note that restoring your device to factory settings will delete all of your personal data.
For information on how to perform a factory reset, please refer to the user manual for your device or consult the manufacturer’s website.
3 - Flash the firmware
If a complete factory reset does not completely removed the infection, it may be necessary to re-flash the firmware on your device, this will essentially reinstall a clean version of the operating system. This is a complex process and we recommend taking your device to a certified engineer.
4 - Change your Google account passwords
Changing the passwords for your Google accounts will reset the authorisation tokens for your device. This will ensure that any tokens obtained by the malware will no longer be valid and will prevent malicious third parties from continuing to access your accounts.
How can I protect myself in future?
- Ensure your operating system (OS) is up-to-date
- Install an anti-virus and have it automatically scan your device on a regular basis
- Only download applications from Google Play or trusted third parties
- Read reviews of the applications you want to download. If the application asks for too much personal data or for permissions that it doesn’t need, avoid it.
What is an email spambot alert?
You might have received a letter and/or email from Virgin Media to explain that we’ve been notified of spam emails originating from a device that uses your home broadband connection. If you have heard from us about this, there’s no need to worry. The advice on this page should help sort things out.
Why has Virgin Media written to me?
We believe a device in your home has been infected with malware that’s sending spam and potentially fraudulent emails to other people on the Internet. We take these types of incidents very seriously, so when we think a customer of ours might have had an infected device, we send them an alert with advice on what to do next.
What’s happened?
We’ve received a report that suggests spam emails are originating from a device on your home network, this is an indicator that one or more of your devices may be infected with a type of malware.
We realise this is unlikely to be your fault, but this kind of abuse is against our Acceptable Use Policy. If the abuse continues we might have to suspend or cancel your broadband service.
For this reason, it’s important you follow the advice in this article.
What can I do about it?
We’re here to help and if you have a basic knowledge of computers and connected devices there are a number of steps you can take to secure your home network. Please apply these steps in order:
1.Check to see if your device has an infection
The easiest way to do this is by using an online virus scanner; some suggested sites are
If you are using an Android or iOS device, you can find a variety of virus scanners on your device’s app store.
2. Use your internet security package to remove any infections
If you have an existing security package installed, please consult the instructions on how to remove infections from your device.
You can register for Virgin Media Internet Security go to My at and register for Virgin Media Internet Security
If you already use Virgin Media Internet Security, make sure "Viruses and spyware scanning" is turned on.
3. Change the passwords for all of your accounts
Once the malware has been removed, you should change the passwords for all the online and email accounts you use.
If any of your passwords were obtained by a malicious third party as a result of the malware infection, it is highly likely they attempted or will attempt to use the same passwords across as many websites and online services as possible, in the hope that the same passwords is used for other accounts you use online.
When changing your passwords, it is important that you use different passwords for all your online accounts and pick strong passwords that are difficult to guess.
4. Get up-to-date software
Keep your operating system and application software up-to-date. Install software patches so that attackers can't take advantage of known problems or vulnerabilities. Many operating systems offer automatic updates. If this option is available, you should enable it.
5. Activate Web Safe
In order to avoid future infections on your home network it is recommended that you turn on Virus Safe, which is available as part of our free Web Safe service which can be found within My Virgin Media. Web Safe will help you block access to web sites known to be infected or to distribute Malware. To access Web Safe just sign in to your account at virginmedia.com/myvirginmedia and select My Apps.
6. Check your contact email address
It is important to provide an up to date contact email address to enable us to advise you of any significant issues that may affect the use of your Virgin Media services. To update your contact email address simply sign in to your account at virginmedia.com/myvirginmedia and select My Profile.
7. Check Auto Forward setting in Virgin Media Mail
In addition, it’s important that you check your mail forwarding rules to ensure that your emails aren’t being forwarded without your knowledge.
To check this in Virgin Media Mail webmail:
- • Go to mail.virginmedia.ie
- • Sign in using your My Virgin Media username and password
- • Click the System Menu icon on the right side of the menu bar and then click the Settings menu item
- • Select the Auto Forward tab
This will display email addresses set to receive forwarded emails from your Virgin Media mailbox. If there is an email address you don’t recognise, and which you didn’t intend to forward your email to, then please select it and delete the forwarding rule.
How do I know I’m now safe?
If you have followed the above advice & have rescanned your device and found it to be clean, you should have resolved the issue.